zero trust to the 5G
-
5G Network Security Solutions
 5G Security Challenges
5G Security Challenges
Security challenges for 5G are the same we see for data in general – network and cost optimization, PKI and root-of-trust, data security, and container security for software delivery. The difference is bad actors may execute attacks by leveraging 5G architecture. The telecom industry has never addressed many of these issues, because they had separate siloed networks and protocols. 5G changes that by allowing virtualization, cloud, hybrid, and shared infrastructures. These bring all the data security challenges of a virtualized and shared environment to 5G.
How can we bring zero trust to the 5G network?
Thales brings trust to 5G by connecting and managing devices, protecting data, and predicting and building resilient networks.
Thales Data Protection Solutions help businesses and service providers protect identities and data in transit, use, and at rest across 5G networks and infrastructure while delivering the low latency and high throughput 5G promises.
Learn how Thales helps help businesses connect and manage millions of devices Mobile Connectivity Solutions and predict and build resilient networks.
Thales data protection solutions for 5G include:
- High-speed network encryption to protect data as it moves across networks
- An integrated encryption and key management platform to secure data and control keys across multi-cloud and hybrid environments
- Hardware security modules (HSMs) for secure crypto operations and PKI infrastructure
- Trusted digital access
Thales 5G security solutions help organizations protect data across fronthaul, midhaul, and backhaul operations as data moves from users and IoT, to radio access, to the edge (including multi-user edge computing), and, finally, in the core network and data stores, including containers.
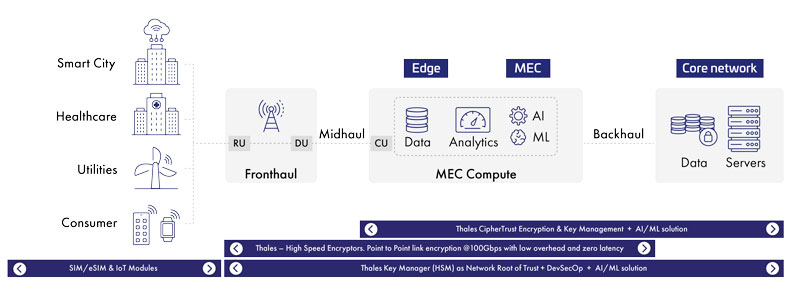
5G Security Solutions for Data In Motion
In the past, telecom networks were primarily hardware-based. With 5G, hardware communicates with virtual machines, virtual machines communicate with virtual machines, containers communicate with containers, and so on. This creates 5G security vulnerabilities, so all this data needs to be protected.
Thales High Speed Encryptors are specifically designed to protect data in motion. They work in Open System Interconnection (OSI) layers 2, 3, and 4 and are three times faster and deliver much lower latency than IPSec. They can be deployed either as hardware or virtual appliances and are FIPS 140-2 level 3, Common Criteria, NATO, and UC APL certified. Our High Speed Encryptors also integrate with quantum security solutions, ensuring relevance for years to come.
5G Security Solutions for Data at Rest
With 5G, data will be stored and manipulated on premises and in the cloud. The best practice for protecting data in containers, in on-premises data centers, in the cloud, or hybrid storage is to encrypt it. CipherTrust Transparent Encryption provides consistent encryption of sensitive data across all network configurations and virtual network functions with granular access control. The solution can be deployed in a Kubernetes infrastructure allowing a containerized application to interact with existing persistent storage. This transparently protects the data. CipherTrust Manager centralizes cryptographic key management across multiple cloud vendors and hardware storage providers.
CipherTrust Transparent Encryption for Kubernetes Security delivers capabilities for encryption, access controls, and data access logging, so organizations can establish strong safeguards around data in dynamic Kubernetes deployments. Specifically, this solution helps protect against unauthorized user access within containers and protect data against privilege escalation attacks from other containers. This solution can also establish isolation between containers, so only authorized containers can access sensitive information.
CipherTrust Transparent Encryption for Kubernetes offers a Container Storage Interface implementation which directly interfaces with the Kubernetes storage layer to protect persistent volumes connected to the containerized application. This offers transparent encryption capabilities without the need to change the application. The solution supports both bare metal and managed Kubernetes deployments for all major platforms, including AWS, Azure, Google, and OpenShift.
Benefits include:
- Transparency: Solution offers encrypting data generated from containerized applications without any change to application business logic
- Scalability: Solution supports deployments using existing Kubernetes orchestration tools to easily expand or shrink the deployments as per the application requirements
- Control: Thales CipherTrust Manager centralizes cryptographic key management across multiple cloud vendors and hardware storage providers
- Auditability: The solution supports access control and provides the capability to audit all file operation/access events to protected data. Users can monitor usage via SIEMs to better understand who is accessing the information.
5G Security Solutions to Protect Identities
In the core network, 5G raises three significant security challenges:
- Subscriber authentication vector generation: Authentication-related keys could be compromised during the authentication process
- 5G subscriber privacy: Insecure subscription permanent identifier (SUPI) encryption key generation, storage, and use could compromise subscriber privacy
- Subscriber key provisioning: Authentication-related keys could be compromised during SIM personalization and provisioning
- 5G Kubernetes Secrets and Dockers containers: Containers running application such as open SSL with cryptographic keys and crypto operations that need to run within the secure boundaries of a FIPS 140-2 L3 hardware Secure Module (HSM)
- PKI Root of Trust: It is paramount to execute all cryptographic functions within a secure environment to ensure both the integrity and the confidentiality of the keys used to encrypt and decrypt data and perform functions such as signing.
Incorporating Thales 5G Luna hardware security modules (HSMs) in the network addresses these issues. 5G Luna HSMs provide extra security to public key infrastructures (PKIs), including digital certificate management for cell towers. In addition, they perform the de-conceal function for SUPI and Subscriber Concealed Identifier (SUCI) mobile applications faster than any other HSM on the market.
Thales 5G Luna HSMs are dedicated crypto processors specifically designed for the protection of the crypto key lifecycle. 5G Luna HSMs act as trust anchors that protect the cryptographic infrastructure of some of the most security-conscious organizations in the world by securely managing, processing, and storing cryptographic keys inside a hardened, tamper-resistant device. Since all cryptographic operations occur within the HSM, strong access controls prevent unauthorized users from accessing sensitive cryptographic material. Thales also implements operations that make deploying secure HSMs as easy as possible. They also integrate with quantum security solutions, making them long-lasting solutions with a good return on investment.


















